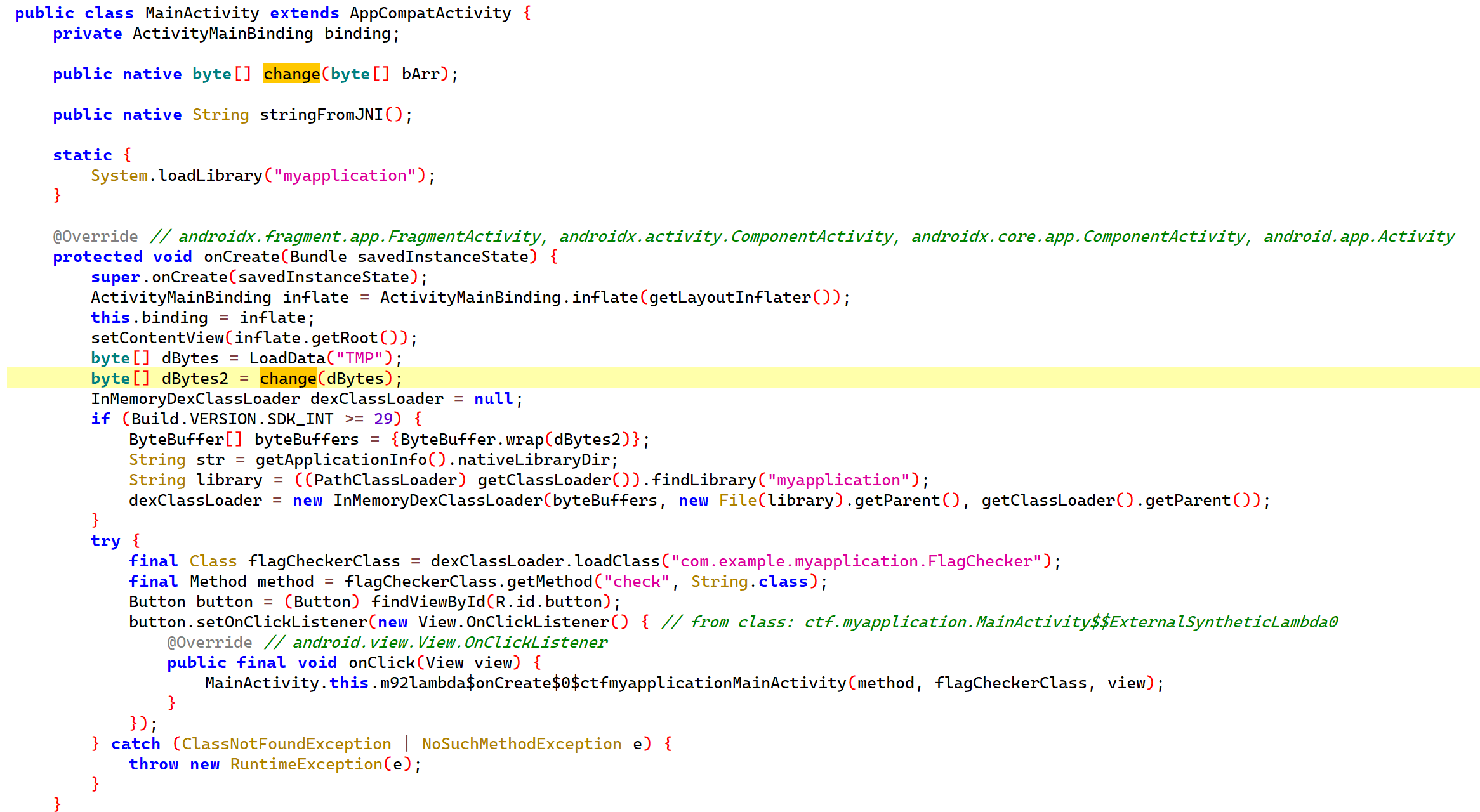
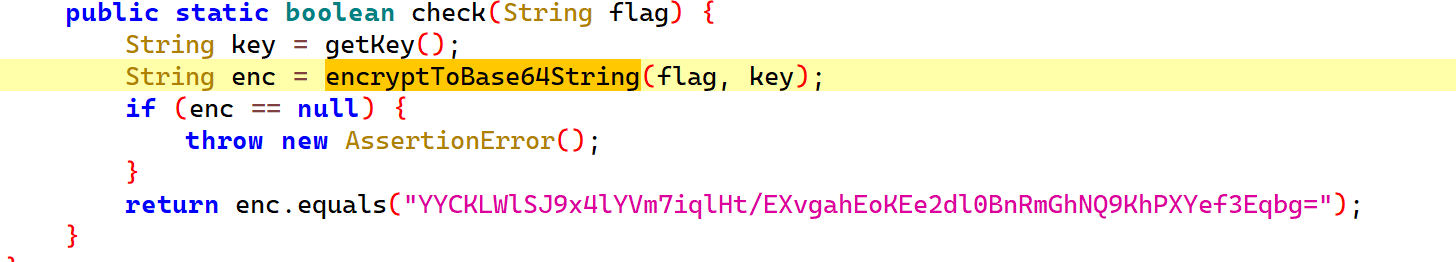
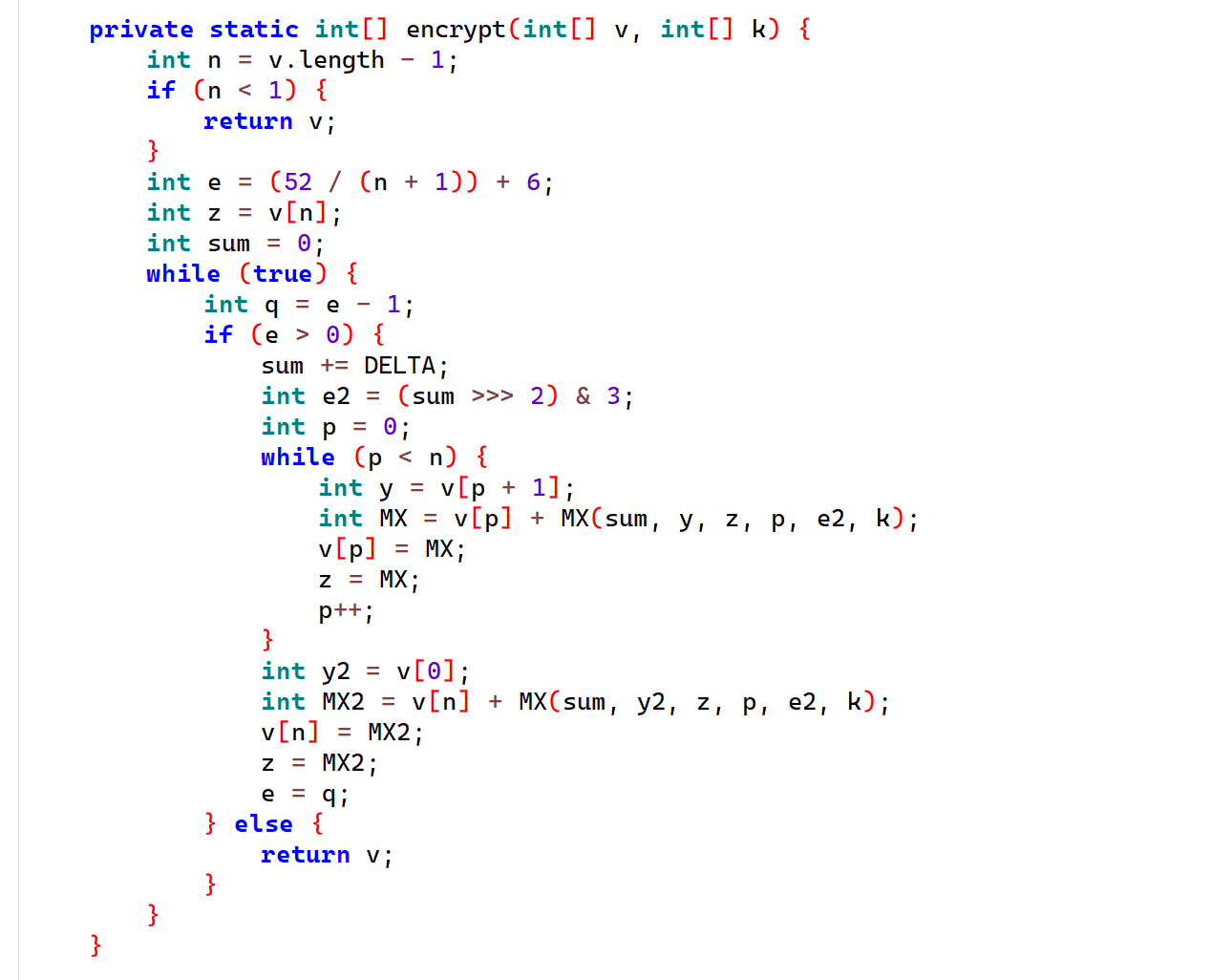
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
| #include <bits/stdc++.h>
using namespace std;
#define MX (((z >> 5) ^ (y << 2)) + ((y >> 3) ^ (z << 4))) ^ ((sum ^ y) + (k[(p & 3) ^ e] ^ z))
void xxteaEncrtpy(uint32_t *v, size_t n, uint32_t *k)
{
uint32_t y, z, sum;
uint32_t p, rounds, e;
uint32_t delta = -1640531527;
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += delta;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
void xxteaDecrypt(uint32_t *v, size_t n, uint32_t *k)
{
uint32_t y, z, sum;
uint32_t p, rounds, e;
uint32_t delta = -1640531527;
rounds = 6 + 52 / n;
sum = rounds * delta;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= delta;
} while (--rounds);
}
int main()
{
char k[] = "882059e204adefc5";
unsigned char v[] = {0x61,
0x80,
0x8a,
0x2d,
0x69,
0x52,
0x27,
0xdc,
0x78,
0x95,
0x85,
0x66,
0xee,
0x2a,
0xa5,
0x1e,
0xdf,
0xc4,
0x5e,
0xf8,
0x1a,
0x84,
0x4a,
0x0a,
0x11,
0xed,
0x9d,
0x97,
0x40,
0x67,
0x46,
0x61,
0xa1,
0x35,
0x0f,
0x4a,
0x84,
0xf5,
0xd8,
0x79,
0xfd,
0xc4,
0xa9,
0xb8};
xxteaDecrypt((uint32_t *)v, 11, (uint32_t *)k);
for (int i = 0; i < 44; i++)
printf("%c", v[i]);
printf("\n");
return 0;
}
|